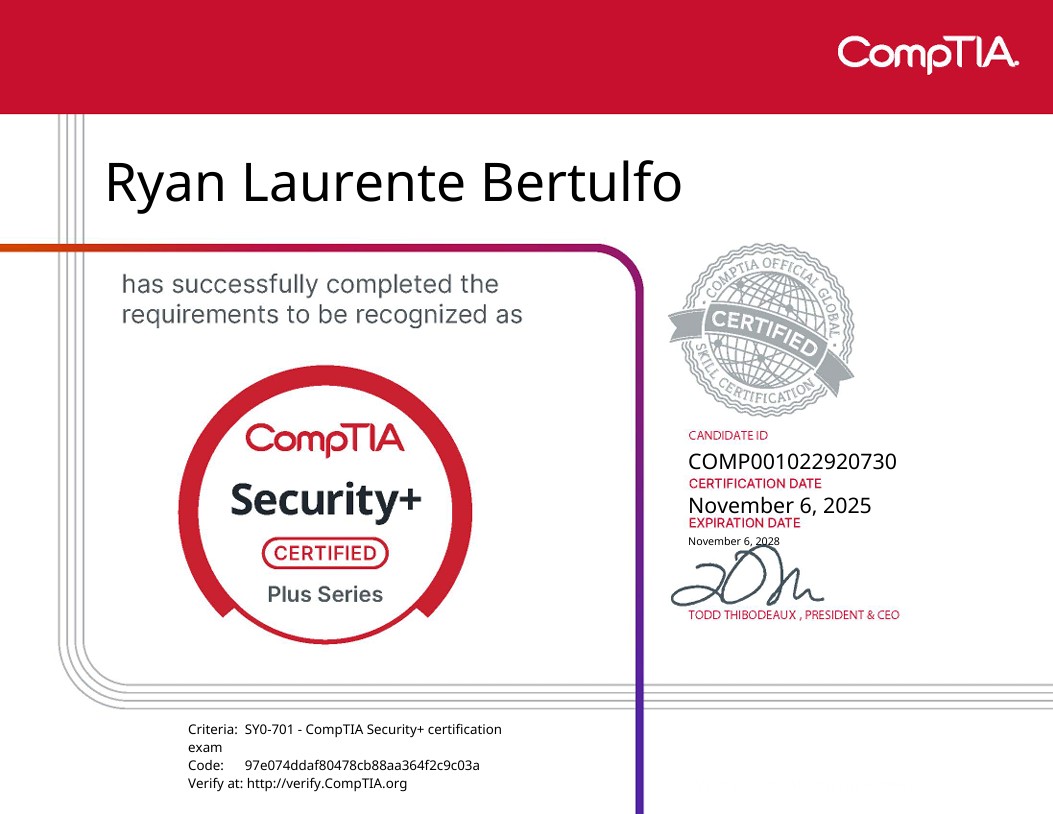
Ryan Bertulfo
Security and Network Operations
About Me
Security Operations Specialist with 6+ years of experience supporting regulated Singapore government environments across network, endpoint, cloud, and security monitoring domains.
My role operates within a hybrid NOC–SOC model, where I perform SIEM alert triage, malware investigation, IOC validation, and incident escalation to L2 SecOps. I regularly analyze telemetry across Splunk, Google Chronicle, and Trend Micro Vision One to distinguish false positives from actionable threats.
My cloud monitoring experience includes reviewing logs and alerts from Amazon CloudWatch, AWS WAF, and AWS Shield to identify anomalous activity within AWS workloads.
Beyond operational responsibilities, I lead an 6-member 24×7 monitoring team, focusing on SLA adherence, incident quality control, and process improvement.
This portfolio documents my hands-on security labs(lnks to GitHub) and detection engineering practice across Wazuh, Elastic, Chronicle, and Splunk environments, where I simulate attacks, build detection logic, and strengthen incident response workflows.
Core Competencies
Security Operations & IR
SIEM & Detection Engineering
Cloud & Infra Monitoring
Ops Leadership
Observability Platform
Government Compliance
Resume
Professional Experience
Senior Infra Executive, Network – Team Lead
NCS Group Singapore (Deployed via Matrix-Process Automation Services)
(Security and Network Operations – Singapore Government Environment)
Acting Team Lead – Network & Security Operations
Jul 2025 - Present
- Lead 6-member 24×7 monitoring team overseeing security alerts, malware investigations, and infrastructure monitoring.
- Serve as escalation authority for validated incidents prior to handoff to L2 SecOps.
- Improved SOP adherence and reduced incident resolution time by 30%.
- Ensure SLA compliance, quality of incident documentation, and alignment with ITIL workflows.
- Coordinate high-impact security findings with agency SIRO/CISO stakeholders.
Senior Infra Executive – Network (NOC & Security Monitoring)
Jul 2018 - Jul 2025
Malware Investigation & IOC Validation
- Investigated malware detections via Trend Micro Vision One, reviewing event metadata, file hashes, execution paths, and endpoint/process activity.
- Conducted hash-based IOC validation, comparing new alerts against historical detection patterns to identify reused files vs. new unknowns.
- Verified alerts against pen test activity and maintenance/patching/Nessus scan windows to eliminate noise and false positives.
- Identified real threats from GCC cloud workloads and escalated qualified incidents to L2 SecOps with supporting evidence.
- Notified and coordinated with agency SIRO/CISO for high-impact or repeated detections, summarizing findings and status.
SIEM Monitoring & Security Analysis
- Reviewed alert metadata and event context across Splunk, and Chronicle for security detections involving endpoint, network, and cloud telemetry.
- Performed preliminary security investigations, validating alert criticality and determining escalation requirements.
- Contributed to monthly IR and incident trend reports, highlighting patterns, repeated detections, and risk observations.
Cloud & Infra Security Monitoring
- Monitored AWS workloads using CloudWatch, WAF, and Shield logs to identify anomalous traffic, brute-force attempts, and suspicious patterns.
- Automated EC2 onboarding/offboarding for security alerting using AWS CloudFormation and integrated CW alarms.
- Supported security monitoring and availability for 2,000+ endpoints, servers, and network devices.
- Configured AWS CloudWatch alarm thresholds and monitored EC2 performance.
Key Achievements
- ✓ Automated EC2 CloudWatch alarms, reducing manual errors
- ✓ Documented and improved shift handover protocols
- ✓ NLB Service Excellence Best Vendor Award (2022-2025)
Help Desk Specialist (Assistant Team Lead)
NCS Group Singapore
- Provided first-level support for 500+ employees with 98% satisfaction rate
- Administered user accounts, VPN, Citrix, SharePoint for 200+ new hires annually
- Collaborated with IT vendors to resolve infrastructure issues
- Generated weekly reports achieving 95% SLA compliance
Education
Bachelor of Science in Information Technology
South Western University
Cebu City, Philippines
Portfolio

ITIL v4 Foundation
IT Service Management AXELOS

Elastic Stack
Great Learning

Qualys Vulnerability Management
Qualys

Data Center Facilities Operations Manager
EXIN CDFOM Certified

Splunk Security Operations and the Defense Analyst
SPLUNK


Active Directory Attack & Defense Lab
End-to-end Active Directory security lab simulating real-world attacks (Kerberoasting, Pass-the-Hash, DCSync) and building custom SIEM detections in Wazuh. Focused on detection engineering, Windows event analysis, and SOC-style troubleshooting rather than tool-only execution.
Advanced Network Forensic Pipeline (BTL1 Aligned)
Built with Python & Streamlit, designed to simulate real-world cybersecurity incident response scenarios by analyzing PCAP files for suspicious patterns, malicious activity, and security anomalies.
Splunk Alert Set Up with Linux and AWS CloudWatch
Basic guide on how to forward Ubuntu machine logs to Splunk using the Universal Forwarder and email alerts for critical events like CPU spikes and multiple login attempts.
Get In Touch
Feel free to reach out for collaborations, opportunities, or just to connect!